You didn't start a business to build cyber security policies and processes from scratch. But we did.
Products
PRODUCTS
Empowering Cyber Resilience
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
Unified Expertise
CX Defenders brings together threat researchers, elite responders, and security consultants to form a cohesive team dedicated to intelligence-driven cyber risk management.
Excellence in Action
Our commitment translates into delivering top-notch threat intelligence, swift incident response, and a transformative approach to security strategy, ensuring unparalleled protection for our clients.
Proactive Cyber Resilience
CX Defenders stands at the forefront of proactive cyber risk management, providing clients with the tools and strategies needed to navigate the evolving digital landscape with confidence and security.
Detection Is
Not Protection
Protect First - With Patented Virtualization.
Then Employ Detection, Verdicting, And Forensic Technologies To Harden Your Environment
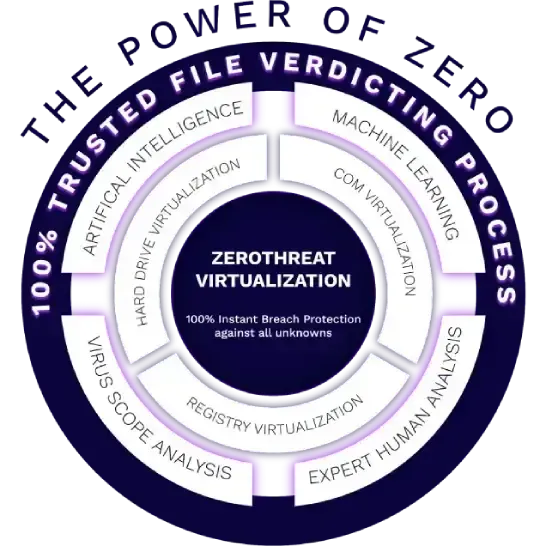
ZeroDwell is a clearcut, proven solution that precedes detection-first security strategies to provide protection from ransomware and malware infections. Meanwhile, it simultaneously eliminates alert fatigue, slashes work loads for your IT and analyst teams, and abolishes big breach remediation budgets.

Win The Race Before It Starts With ZeroDwell Time
Cyber security shield reduces the amount of time a threat can maneuver or dwell in your environment, down to absolute zero. ZDC is the foundation of ZeroDwell's instantaneous kernel-level virtualization of unknown at runtime.
Attacks happen in minutes and seconds. But the impact from an attack does not always occur instantly. It can take some dwell time for an intruder to get a foothold and enumerate to execute search and destroy or exfiltration missions. Cyber security shield ZDC intercepts and isolates the attack before any of its impact and intended damage can occur.
It's a race, and Cyber security shield leads with a disruptive, strategic offense. ZeroDwell provides an unfair advantage for defenders. When it comes to unknown entering your endpoints, we protect first, then ask questions and identify, detect and verdict second. That's Cyber security shield unique advantage.
Cyber security shield Enterprise Platform
PRODUCTS
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
ENDPOINT
CLOUD
NETWORK
INTERNET
MANAGED
DID YOU KNOW?
WE PREVENT CYBERATTACKS & BREACHES THROUGH INNOVATION
we understand the Challenges!
There are two Scientific challenges in Endpoint Security today

HALTING PROBLEM
An undecidable Problem in Computer Science
Alan Turing proved in 1936 that a general algorithm (software code) running on a Turing machine that solves the halting problem for all possible program-input pairs necessarily cannot exist. Hence, the halting problem is undecidable for Turing machines....

DEFAULT ALLOW POSTURE
There are two security postures for the endpoint security...Default Allow...Default Deny...
Default Allow: Allow everyone in but known bad. Look for bad indicators...allow everyone in who does not have bad indicator
WHY US
ENTERPRISE PLATFORM OUR VALUE PROPOSITION FOR YOU

WE PREVENT BREACHES
Click on anything
Run any software
No more Dwell time
No more False positives
No more remediation
No more chasing tail "trying to detect"
WE AUTOMATICALLY CONTAIN THE "UNKNOWN"
The Unknown file is the enemy.
We "Temporarily" run the unknown in our patented Containment (CPU-enforced OS Virtualization)
ALL THREAT VECTORS COVERED
EXEs, DLLs, emails, USB files
Day zero attacks
All known attacks
fileless malware
Any and every malicious code..known or unknown
Full Forensic analysis report on every malware
WE UNDERSTAND FILE STATES
(World's Only Company to do so)
File exist in 3 states...
Good, Bad & Unknown
Allow Good...
Stop Bad..
Automatically Contain Unknown
(in CPU Enforced OS Virtualization)
WE GIVE EVERY FILE A VERDICT
Once an unknown file is contained...
We will give each and every file 100% Trusted Verdict!
We Don't do "Assumption" based verdicts
We provide SLA for our Verdicts
We use Human Analysts for 100% trusted verdicts.
You will KNOW EVERY FILE in your Network!
You can say: I KNOW there is no Malware in my Network!
AMAZINGLY LOW RESOURCE REQUIREMENTS
Less than 20Mb
Less than 1% of CPU
Works even with XP
Processor agnostic
Battle tested with over 85Million endpoints(The only CPU Enforced OS Virtualization with this many endpoints)
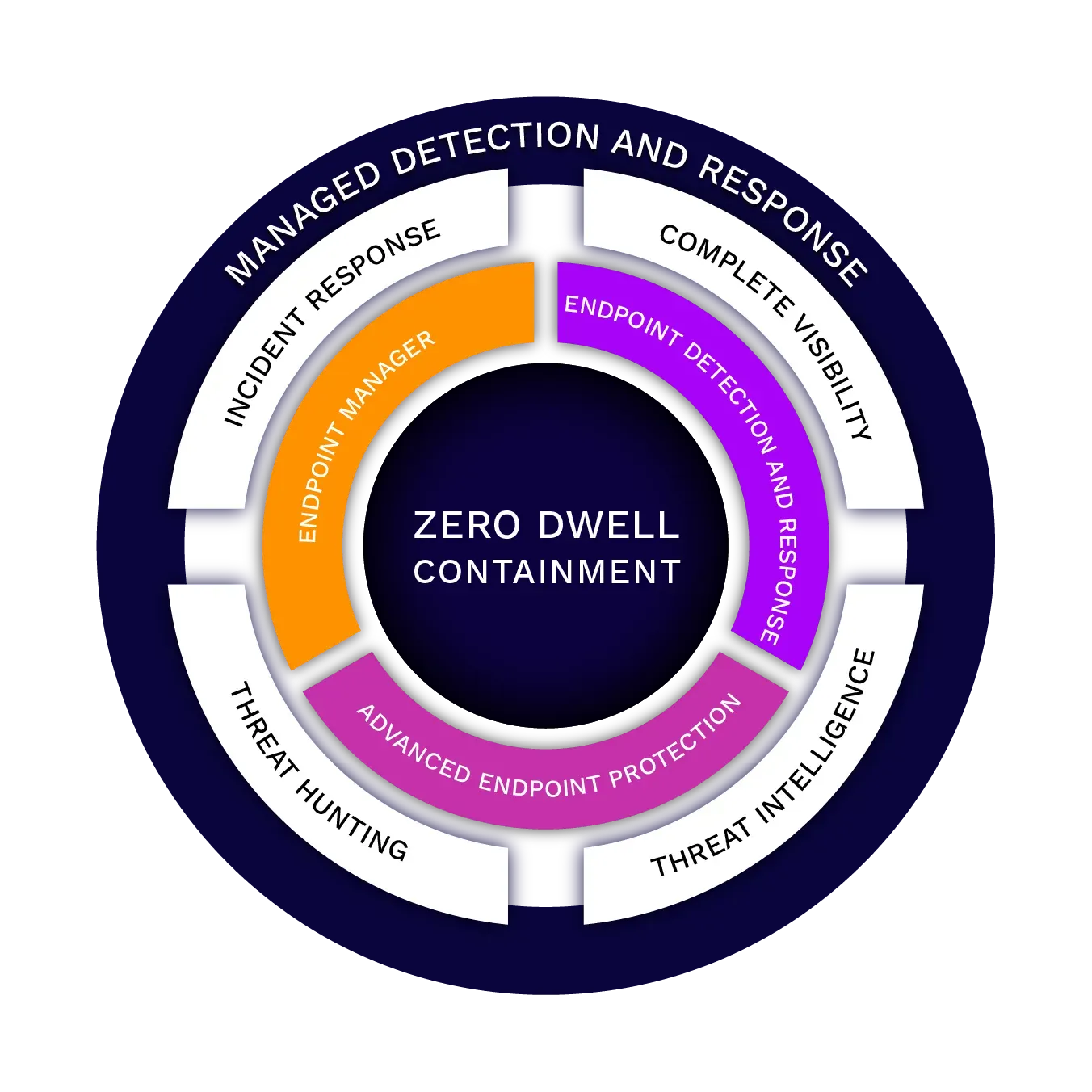
Cyber security shield MANAGED DETECTION AND RESPONSE
24/7 decision support for answers, not alerts
MDR that safeguards your cloud, Kubernetes, on-prem, and SaaS environments

Get answers,
not alerts
We provide 24/7 MDR services across cloud, Kubernetes, SaaS and on-prem. Through a software-driven approach, our MDR services eliminate the noise and prioritize what matters to your business — with speed, accuracy and transparency.
HOW Cyber security shield IS DIFFERENT
Resolve incidents faster with an automated approach
Our managed detection and response service is powered by our security operations platform, CX Defend Workbench. Once you connect your tech, alerts are analyzed by the CX Defend Workbench platform with an alert review of less than 1 minute. We’ll add context, enrich with intel and assess the risk to auto-remediate or send to an analyst for further investigation.
You get the best of both technology and people—all with an average MTTR of only 22 minutes.

Integrate the tech you already have
Connect your tech — no agents, new hardware (or even a SIEM). We’ll apply custom detections and learnings to gain deeper insight and improve ROI.
Get the right automation at the right time
We automate logs, alerts and can auto-remediate on your behalf, or we’ll provide full resilience recommendations for you to resolve.
Filter out noise with context
Our Security Operations Center investigates only the interesting events that require further analysis, so you get immediate answers to the alerts that matter the most.
Get transparency all day, every day
Get complete visibility into the investigation process through real-time alerts when incidents arise and intuitive reporting to prevent the risk from occurring again.
Products
CX Shield Advanced (EPP+EDR)
There’s no question there is a need for EDR. Yet, detection-first EDR tools provide insufficient EDR security. Attackers are smart. They understand how detection-first EDR solutions work, and they continuously develop techniques to slip under everyone’s radar to attack as “Unknowns.” Unknowns cannot be detected. But when you add EDR protection-first, real-time ZeroDwell Containment to an EDR solution’s front end, suddenly you experience a paradigm shift and see breaches and ransom incidents plummet.

CX Complete Advanced EDR Threat Preventiona
ZeroDwell Xcitium Advanced EDR technology delivers auto-isolation services that complement your existing endpoint protection platform or security posture. This Advanced EDR standalone product includes a SaaS management console, endpoint client agents, Advanced EDR service delivery from the Threat Research Labs (TRL), and the Verdict Cloud engine, a file safety determination service used to assess isolated files and objects to EDR provide a malicious or safe verdict about contained Unknowns.
CX shield Advanced Minimize User Impact
Once CX shield Advanced EDR is deployed it has less than minimal resource usage. End users enjoy seamless productivity, with the ability to run any unknown CX shield Advanced EDR file virtually, even while the file is in CX shield Advanced EDR analysis.

CX Shield Advanced Trusted Verdicts/Verdict Cloud engine + threat intel
Through the Verdict Cloud engine, results are published globally in real-time for all CX shield Advanced EDR customers. Using a combination of multiple AI Advanced EDR environments and human security specialists, you will never be exposed to the damage of cyber threats through true EDR zero-trust architecture.
WHY US
Advanced Feature Capabilities

ZeroDwell Containment
Prevents unknowns instantly through denying write access privileges of any unknowns
NGAV & Award-winning Firewall
Powerful real world antivirus to automatically detect, cleanse and quarantine suspicious files
Fileless Malware Protectiona
Protection against fileless malware payloads that bypass any traditional antivirus
Verdict Cloud Intel Analyzers
Real time static and dynamic scans across the cloud, deep web, and dark web for unknowns against your organization.
Cloud Based Updates
New malware signatures are consistently delivered through the cloud to ensure both security and optimal user performance.
Virus Scope Behavior Analyzer
Closely monitors behavior anomalies of all processses to identify any potentially harmful actions before they happen.
Host Firewall
Keep incoming threats out as well steer clear of any suspicious threats going outbound.
Host Intrusion Prevention System
Continuous monitoring of operating system activities to detect intrusions before any trespassing can occur
Xcitium File Reputation Lookup
Cross reference any file’s threat reputation against one of the world’s largest whitelist and blacklist threat intelligence.
Products
CX Shield Complete XDR
Access operational ease with rich, built-in XDR integrations across the entire security tech stack providing XDR deep visibility, XDR real-time context, automated containment, CX Shield Complete XDR detection, and Complete XDR response. Only actionable alerts/ no alert fatigue. A fully integrated Xcitium Complete XDR platform means a significant reduction in the total cost of ownership.

Managed Extended Detection And Response
Complete XDR)
MXDR extends across endpoints to continuously Complete monitor, manage, and Complete XDR connects the dots across your entire Complete XDR technology stack. Our Kernel-level ZeroDwell virtualization is a pre-emptive prevention technology that precedes Complete XDR detection and response by containing Unknowns and potential Complete attacks at runtime.
24•7•365 Continuous Monitoring
Leverage a 24x7x365 team of highly skilled SOC Complete XDR analysts to conduct in-depth investigations. Receive Complete XDR high-fidelity threat notifications for attacker activity, malicious programs, & suspicious behavior.
Threat Intelligence Integrations
Receive highly refined internal & external threat intelligence feeds to XDR alert or block Indicators of Compromise. Incorporate Complete XDR your internal intelligence into Enterprise Platform for added coverage.
Our Verdict Cloud integration checks on process execution via hash submission and delivers Complete static analysis, kill-chain reporting, & human reverse engineering.

Real-Time Response & Reporting
Complete XDR Enterprise platform enables our responders to automate the forensic collection process, block activity in real-time, isolate endpoints from the network, execute custom commands, and provide live responses to your remote Complete systems for remediation.

Proactive Threat Hunting Complete XDR
An Complete XDR team of highly trained cybersecurity experts will continuously hunt through generated logs looking for anomalous and suspicious activity across your XDR organization. Your environment will be baselined for known good behavior and Complete XDR ZeroThreat Complete MDR will alert you on deviations outside those recorded patterns.
Collected endpoint telemetry XDR also provides threat hunters with the foundation they need to find stealthy, novel attacks while leaving no stone unturned.

Complete XDR Incident Response
Our Complete Incident Response team is readily available to conduct in-depth forensic investigations. Receive a detailed timeline of attack activity derived from digital forensics. In Complete XDR addition to Complete Technology telemetry, this includes analysis of artifacts such as $MFT, Windows Event Logs, Registry, Web History, etc. After a breach or incident, our team guides you through the next best steps to protect your XDR endpoints, XDR network, and assets.
This Complete XDR includes threat neutralization and remediation support.

